Diaphora
Diaphora, the most advanced Free and Open Source program diffing tool
介绍
This is the official Liberapay page of Diaphora (διαφορά, Greek for 'difference') version 3.1.2, the most advanced program diffing tool, in the form of an IDA plugin. It was released first in 2015 and has been actively maintained since this year porting and testing it for every single minor version of IDA since 6.8 to 8.4. It's actively maintained and improved every year, adding multiple new features not available in any other binary diffing tool.
Diaphora supports versions of IDA from 7.4 up to 8.4, the latest version as of February 2024.
What your donation is for
Donating on this page directly funds the author and maintainer of Diaphora, and it also helps paying the domain name, as well as the future servers hosted in Digital Ocean that will be used in server versions of Diaphora (still under development).
Unique Features of Diaphora
Diaphora has many of the most common program diffing (bindiffing) features you might expect, like:
- Diffing assembler.
- Diffing control flow graphs.
- Porting symbol names and comments.
- Adding manual matches.
- Similarity ratio calculation.
- Batch automation.
- Call graph matching calculation.
- Dozens of heuristics based on graph theory, assembler, bytes, functions' features, etc...
However, Diaphora has also many features that are unique, not available in any other public tool. The following is a non extensive list of unique features:
- Ability to port structs, enums, unions and typedefs.
- Potentially fixed vulnerabilities detection for patch diffing sessions.
- Support for compilation units (finding and diffing compilation units).
- Microcode support.
- Parallel diffing.
- Pseudo-code based heuristics.
- Pseudo-code patches generation.
- Diffing pseudo-codes (with syntax highlighting!).
- Scripting support (for both the exporting and diffing processes).
- ...
Screenshots
Diaphora finding the exact function where a vulnerability was patched in CVE-2020-1350:
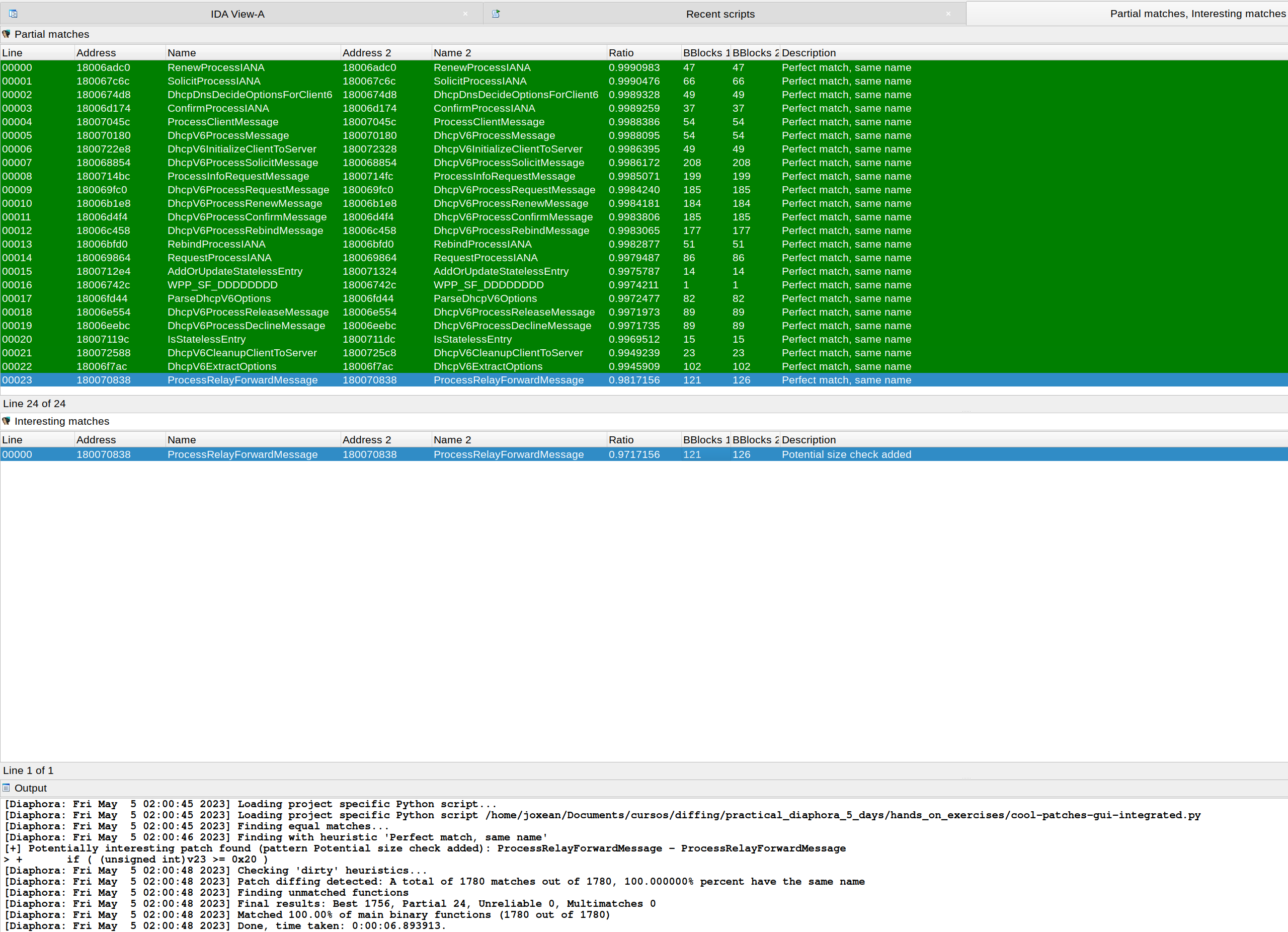
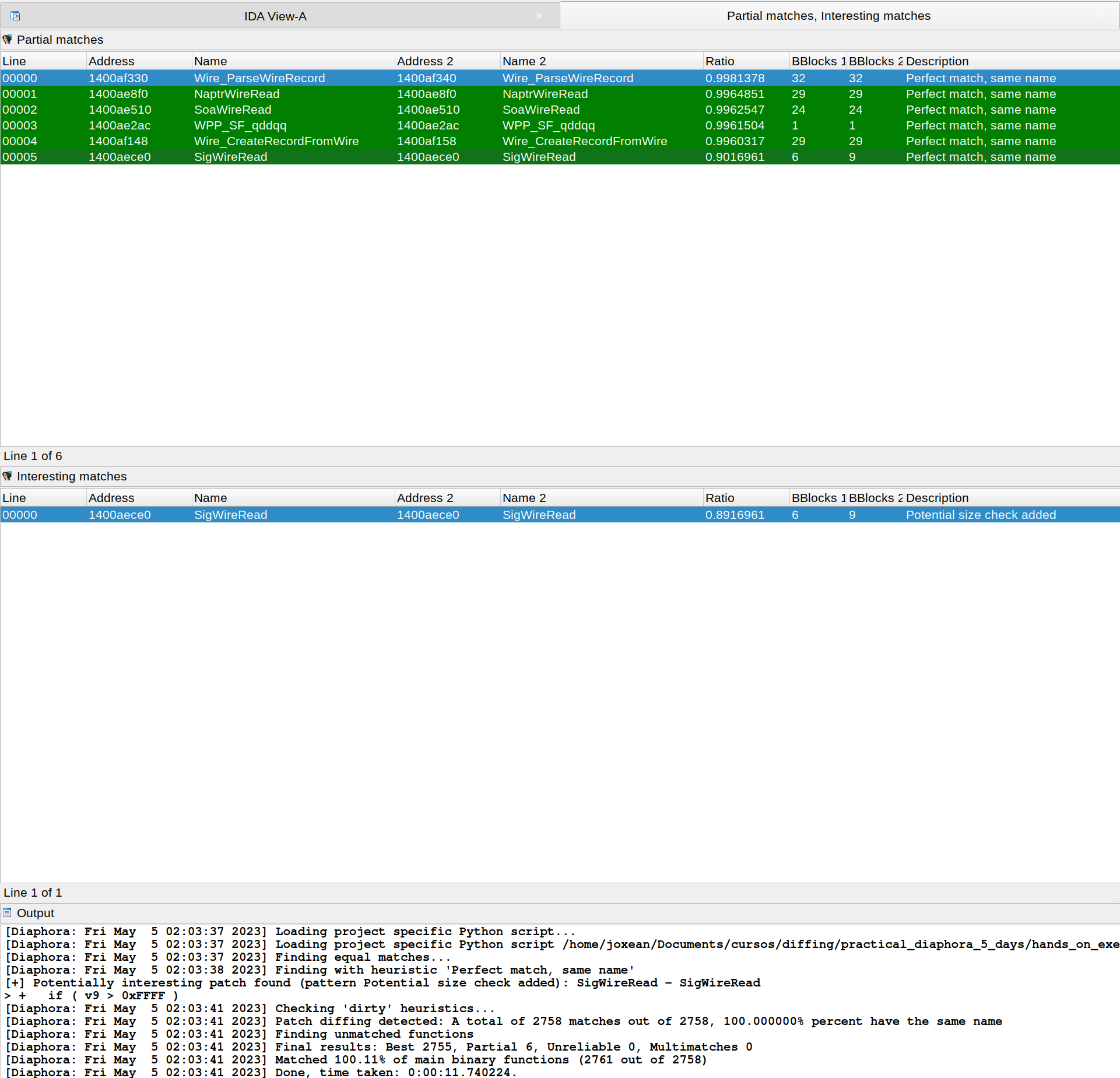
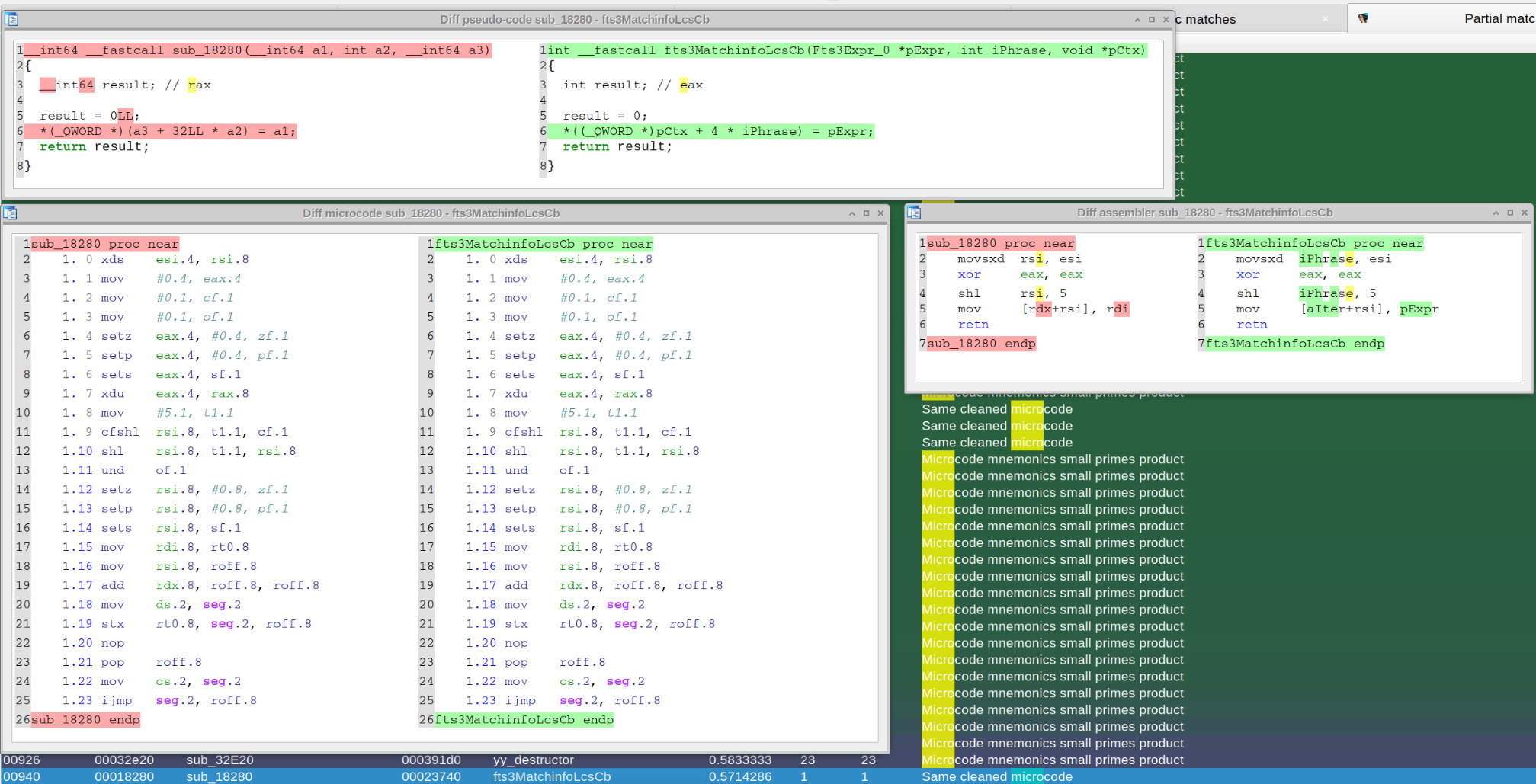
Diaphora, again, finding the exact function where CVE-2023-28231 was fixed:
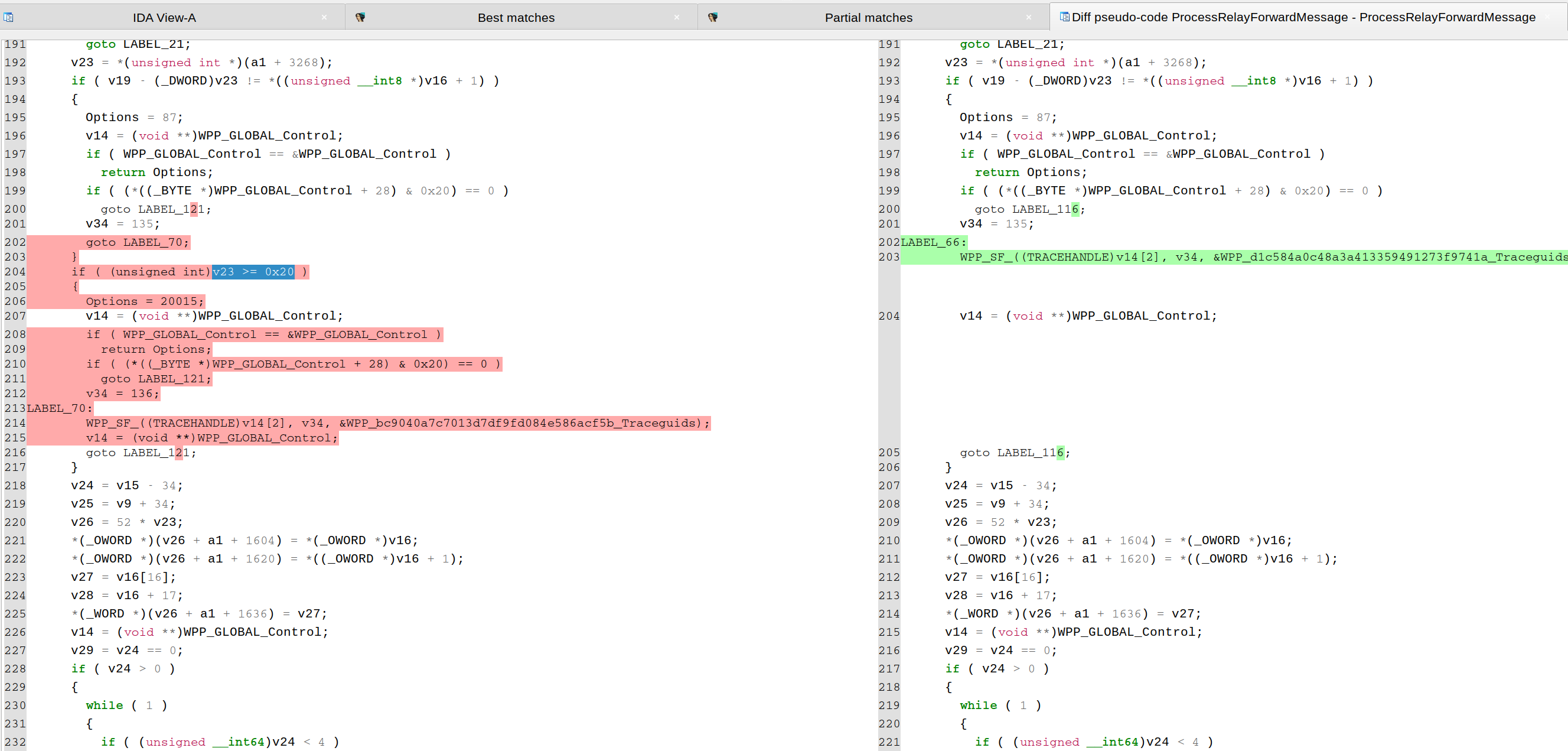
CVE-2023-28231. As explained in a blog from ZDI, the vulnerability was fixed by checking that the number of relay forward messages in "ProcessRelayForwardMessage()" is not bigger or equal than 32 (0x20), as shown in the following pseudo-code diffing:
Diaphora doing Hex-Ray's microcode diffing:
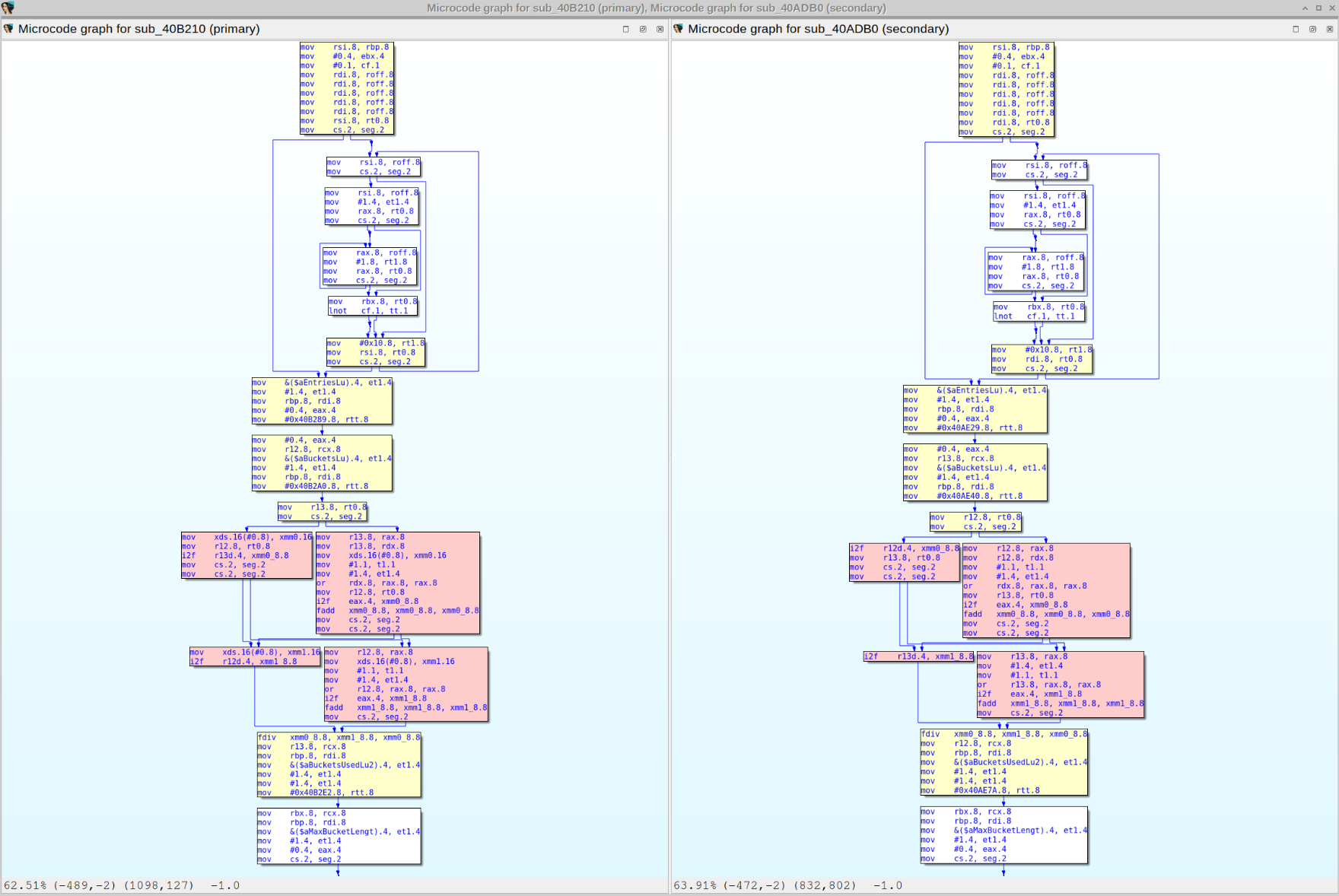
Diffing assembly, pseudo-code and microcode:
Diffing CVE-2023-21768 with Diaphora 3.0:
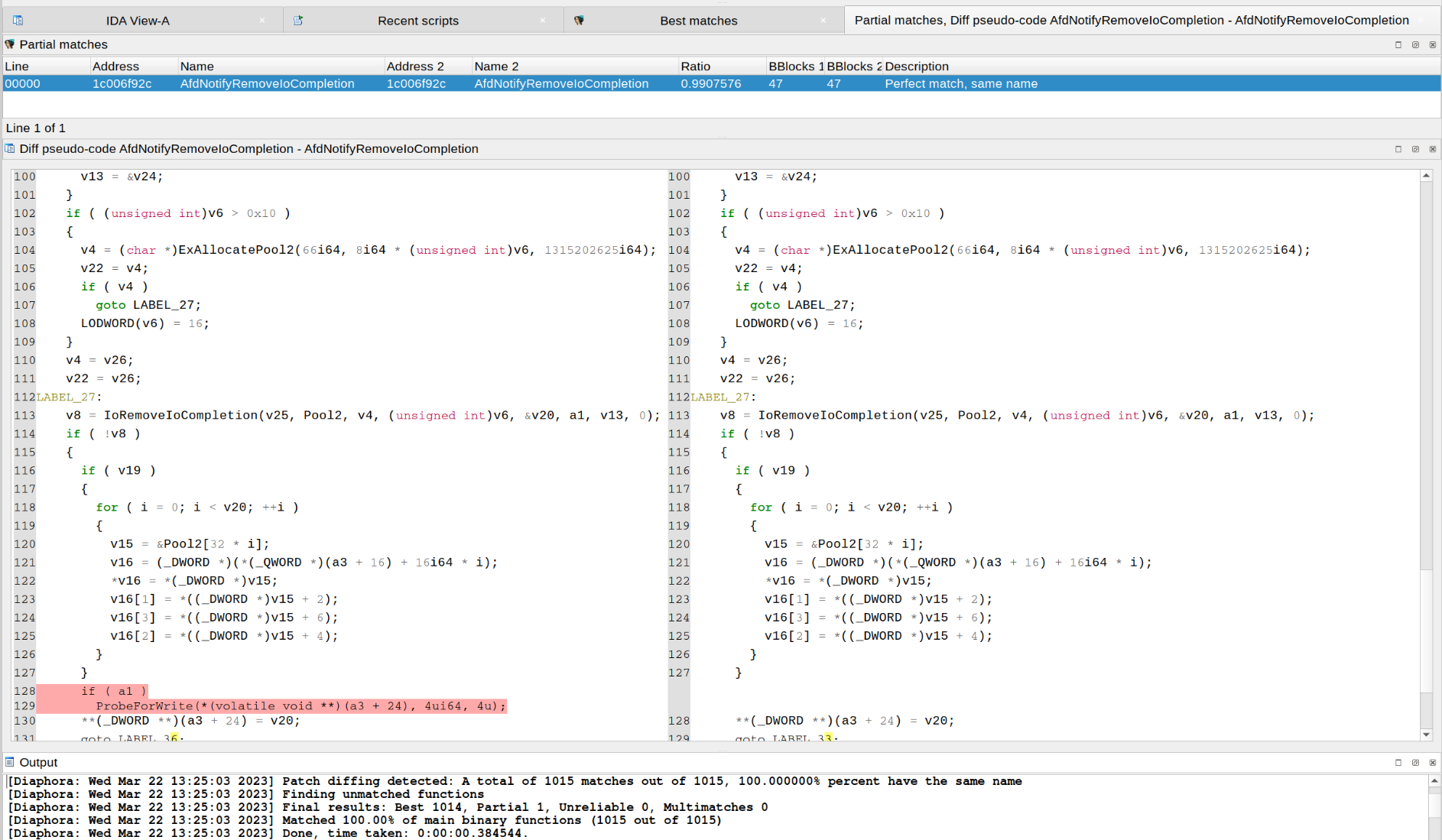
This is a screenshot of Diaphora diffing the PEGASUS iOS kernel Vulnerability fixed in iOS 9.3.5:
And this is an old screenshot of Diaphora diffing the Microsoft bulletin MS15-034:
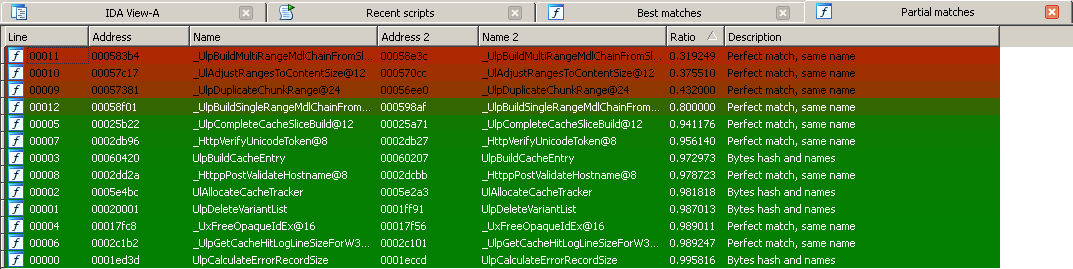
These are some screenshots of Diaphora diffing the Microsoft bulletin MS15-050, extracted from the blog post Analyzing MS15-050 With Diaphora from Alex Ionescu.
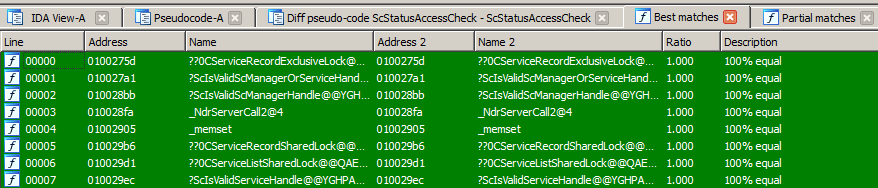
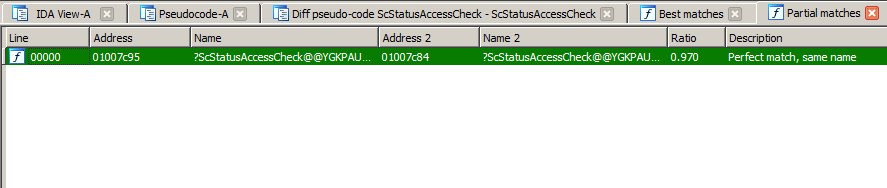
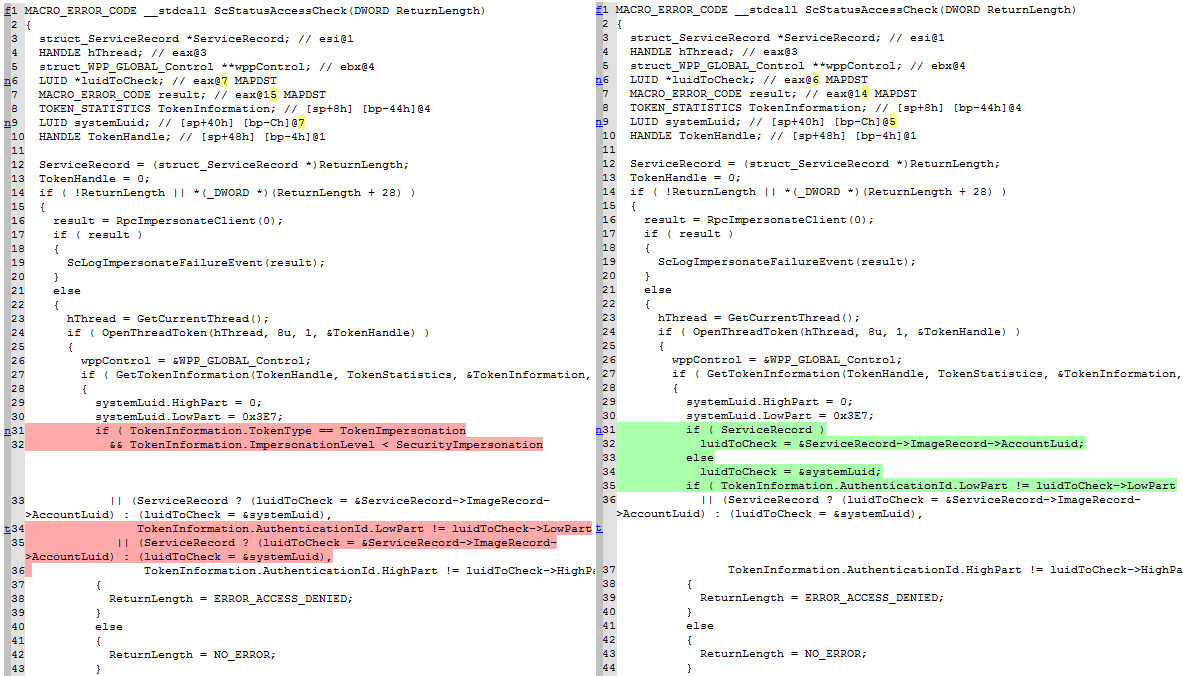

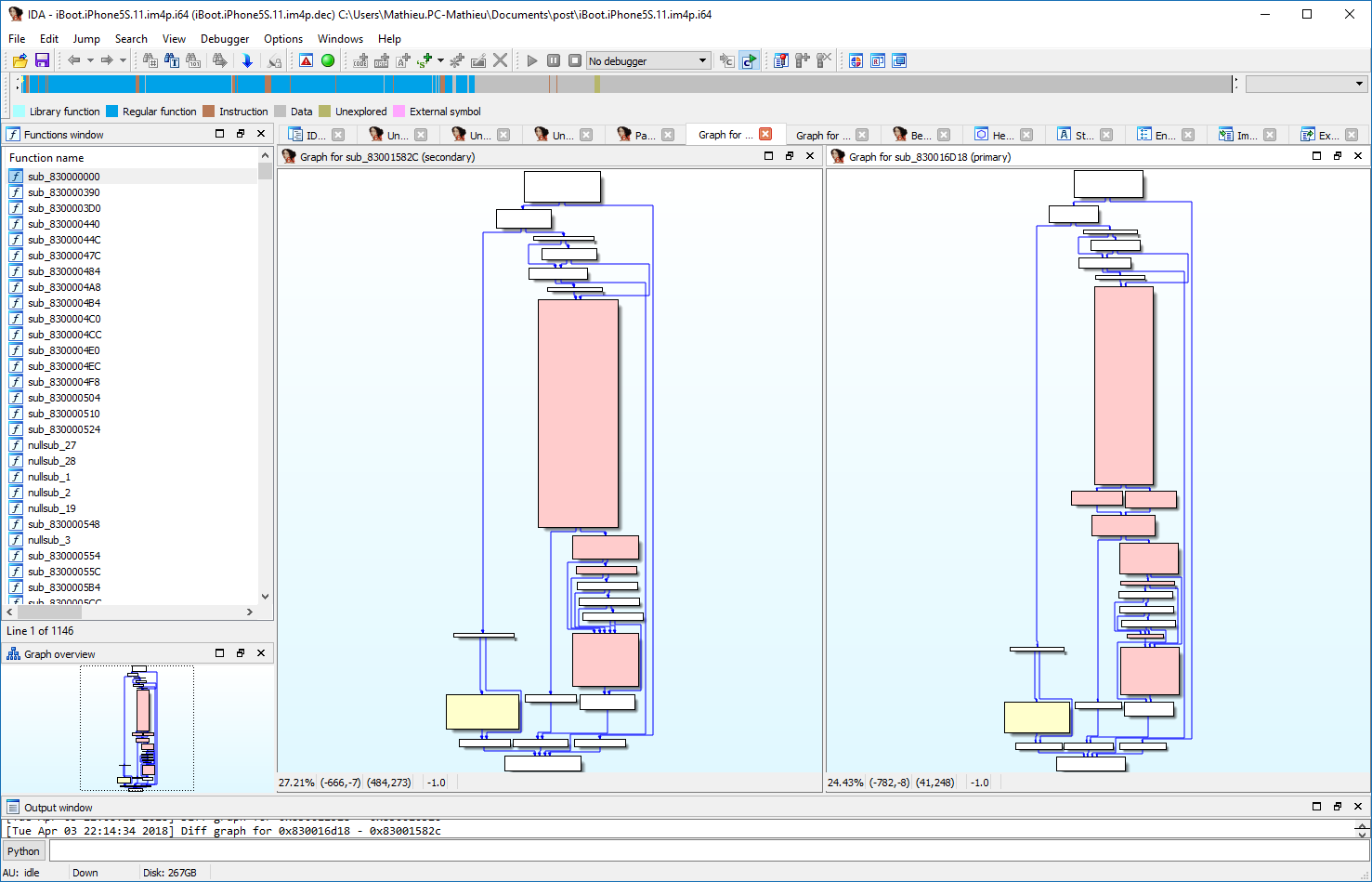
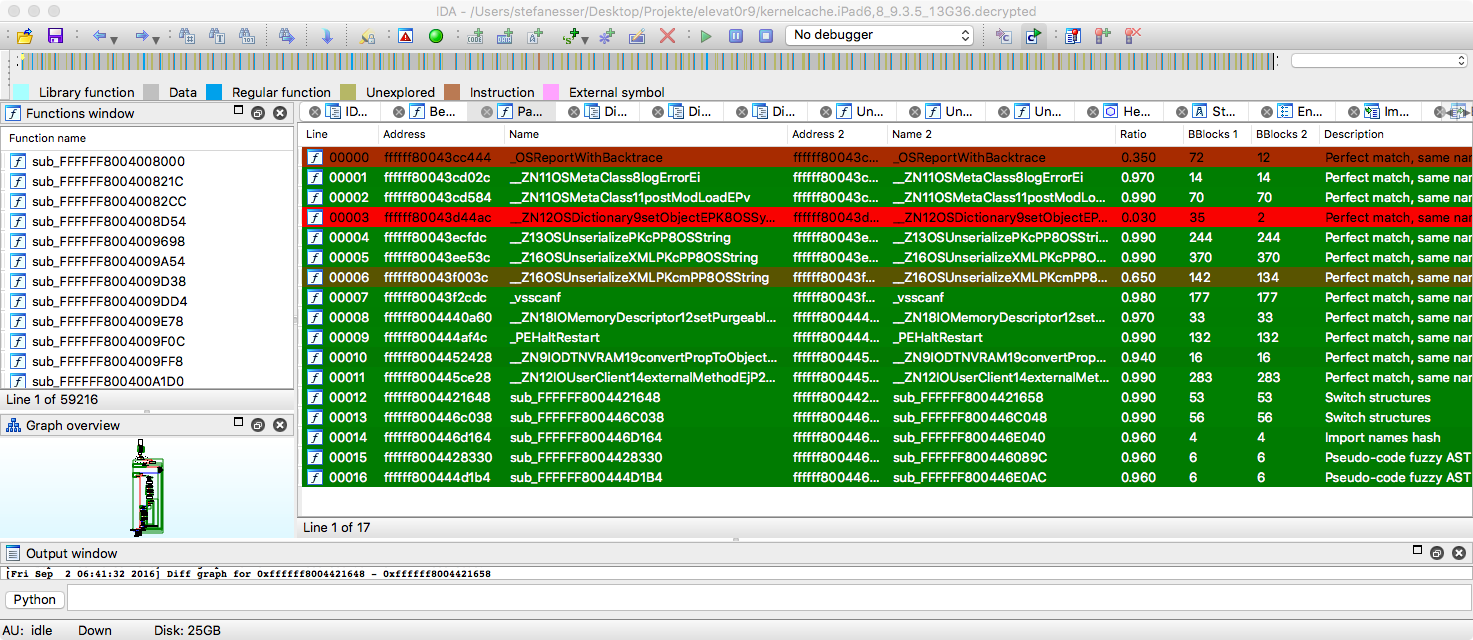
Here is a screenshot of Diaphora diffing iBoot from iOS 10.3.3 against iOS 11.0:
Download Diaphora
Diaphora is Free Software. Get it at: https://github.com/joxeankoret/diaphora
已链接的账号
Diaphora 持有其他平台上的下列账号:
代码库
diaphora 星标数 3606 本周更新
Diaphora, the most advanced Free and Open Source program diffing tool.
赞助者 导出 CSV
Diaphora 有 1 名公开赞助人。
记录
Diaphora 在 1年前 加入。